Easy Vpn Vs Flexvpn Vs Getvpn Vs Dmvpn
Virtual Private Networks constitute a hot topic in networking because they provide low cost and secure communications between sites (site-to-site VPNs) while improving productivity by extending corporate networks to remote users (remote access VPNs).
Cisco must be proud of its VPN solutions. It's one of the few vendors that support such a wide range of VPN technologies with so many features and flexibility. Cisco Routers and Cisco ASA Firewalls are the two types of devices that are used most often to build Cisco Virtual Private Networks.
In this article we will discuss and compare two general Cisco VPN categories that are utilized by network engineers to build the majority of VPN networks in today's enterprise environments. These categories are "Policy Based VPNs" (or IPSEC VPNs) and "Route Based VPNs". Of course Cisco supports additional VPN technologies such as SSL VPNs (Anyconnect SSL VPN, Clientless SSL VPN), Dynamic Multipoint VPN (DMVPN), Easy VPN, Group Encrypted Transport (GET) VPN etc. Many of these VPN technologies are already covered on Firewall.cx and are beyond the scope of this article.
Below is a selection of Cisco VPN articles to which interested users can refer:
- Understanding Cisco Dynamic Multipoint VPN (DMVPN)
- Dynamic Multipoint VPN (DMVPN) Deployment Models & Architectures
- Configuring Cisco Dynamic Multipoint VPN (DMVPN)
- Configuring Site to Site IPSec VPN Tunnel Between Cisco Routers
- Configuring Cisco Site to Site IPSec VPN with Dynamic IP Endpoint Cisco Routers
- Configuring Point-to-Point GRE VPN Tunnels on Cisco Routers
- Cisco GRE and IPSec - GRE over IPSec - Selecting and Configuring GRE IPSec Tunnel or Transport Mode
- Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco IOS Routers
Overview of Policy-Based and Route-Based Cisco VPNs
The diagram below shows a quick overview of the two VPN Categories we are going to discuss and their Practical Applications in actual networks:
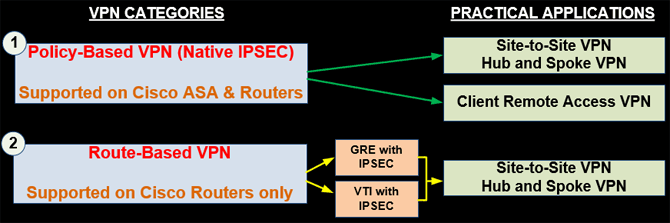
For a Network Engineer or Designer it's important to know the main differences between these two VPN categories and their practical applications. Knowing these will help professionals choose the right VPN type for their company and customers.
As shown in the diagram above, Policy-Based VPNs are used to build Site-to-Site and Hub-and-Spoke VPN and also remote access VPNs using an IPSEC Client. On the other hand, Route-Based VPNs are used to build only Site-to-Site or Hub-and-Spoke VPN topologies.
Now let's see a brief description of each VPN Type.
Policy-Based IPSEC VPN
This is the traditional IPSEC VPN type which is still widely used today. This VPN category is supported on both Cisco ASA Firewalls and Cisco IOS Routers. With this VPN type the device encrypts and encapsulates a subset of traffic flowing through an interface according to a defined policy (using an Access Control List). The IPSEC protocol is used for tunneling and for securing the communication flow. Since the traditional IPSEC VPN is standardized by IETF, it is supported by all networking vendors so you can use it to build VPNs between different vendor devices as well.
Sample Configuration on Cisco ASA Firewalls
To illustrate the reason why this VPN type is called Policy-Based VPN, we will see a sample configuration code on a Cisco ASA firewall based on the diagram below.
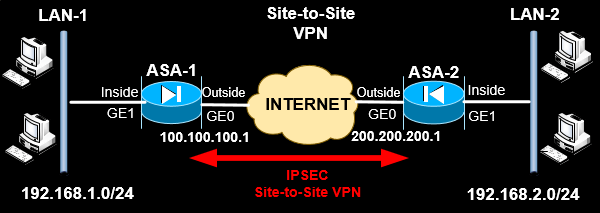
Full step-by-step configuration instructions for Policy-Based VPN on IOS Routers can be found at our Configuring Site to Site IPSec VPN Tunnel Between Cisco Routers article.
ASA-1:
ASA-1(config)# access-list VPN-ACL extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
ASA-1(config)# crypto ipsec ikev1 transform-set TS esp-aes esp-md5-hmac
ASA-1(config)# crypto map VPNMAP 10 match address VPN-ACL
ASA-1(config)# crypto map VPNMAP 10 set peer 200.200.200.1
ASA-1(config)# crypto map VPNMAP 10 set ikev1 transform-set TS
ASA-1(config)# crypto map VPNMAP interface outside
ASA-2:
ASA-2(config)# access-list VPN-ACL extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
ASA-2(config)# crypto ipsec ikev1 transform-set TS esp-aes esp-md5-hmac
ASA-2(config)# crypto map VPNMAP 10 match address VPN-ACL
ASA-2(config)# crypto map VPNMAP 10 set peer 100.100.100.1
ASA-2(config)# crypto map VPNMAP 10 set ikev1 transform-set TS
ASA-2(config)# crypto map VPNMAP interface outside
From the configuration sample above, the access control list VPN-ACL defines the traffic flow that will pass through the VPN tunnel. Although there is other traffic flowing through the outside ASA interface, only traffic between LAN1 and LAN2 will pass through the VPN tunnel according to the traffic policy dictated by VPN-ACL. That's exactly the reason why this VPN type is called Policy-Based VPN.
Understanding Route-Based VPNs
A route-based VPN configuration uses Layer3 routed tunnel interfaces as the endpoints of the VPN. Instead of selecting a subset of traffic to pass through the VPN tunnel using an Access List, all traffic passing through the special Layer3 tunnel interface is placed into the VPN. Therefore you need to configure routing accordingly. Either a dynamic routing protocol (such as EIGRP or OSPF) or static routing must be configured to divert VPN traffic through the special Layer3 tunnel interface.
This VPN Type is supported only on Cisco Routers and is based on GRE or VTI Tunnel Interfaces. For secure communication, Route-Based VPNs use also the IPSEC protocol on top of the GRE or VTI tunnel to encrypt everything.
Sample Configuration on Cisco Routers
Based on the network diagram below, let's see a GRE Route-Based VPN with IPSEC Protection.
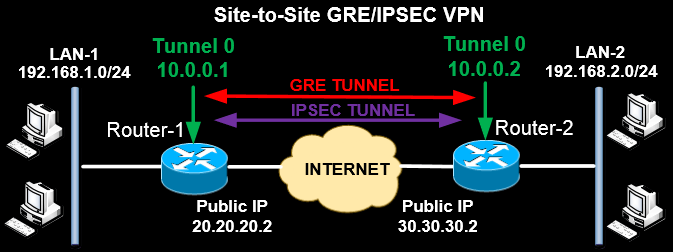
Full step-by-step configuration instructions for Route-Based VPN on IOS Routers can be found at our Configuring Point-to-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE over IPSec Tunnels article.
Router-1:
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
crypto ipsec profile GRE-PROTECTION
set transform-set TS
!
interface Tunnel0
ip address 10.0.0.1 255.255.255.0
tunnel source 20.20.20.2
tunnel destination 30.30.30.2
tunnel protection ipsec profile GRE-PROTECTION
!
ip route 192.168.2.0 255.255.255.0 10.0.0.2
!
From the configuration above, a GRE Layer3 Tunnel Interface is created (Tunnel0) which will be one of the endpoints of the VPN tunnel. IPSEC Protection is also applied for security. The other end of the VPN tunnel is Tunnel0 of the other site (with IP 10.0.0.2), thus forming a point-to-point VPN link. The static route shown above will divert VPN traffic destined for LAN2 via the Tunnel Interfaces.
Following is the VPN related configuration commands for our second router:
Router-2:
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
crypto ipsec profile GRE-PROTECTION
set transform-set TS
!
interface Tunnel0
ip address 10.0.0.2 255.255.255.0
tunnel source 30.30.30.2
tunnel destination 20.20.20.2
tunnel protection ipsec profile GRE-PROTECTION
!
ip route 192.168.1.0 255.255.255.0 10.0.0.1
!
Comparison Between Policy-Based and Route-Based VPNs
To summarize, let's see a comparison table with the main differences between Policy-Based and Route-Based VPNs.
| Policy-Based IPSEC VPN (Traditional IPSEC) | Route-Based VPN (GRE and VTI) |
| Supported on most network devices (Cisco Routers, Cisco ASA, other vendors etc) | Supported only on Cisco IOS Routers. Very limited interoperability with other vendors |
| Does not support multicast or non-IP protocols | Supports multicast (GRE and VTI) and non-IP protocols (GRE) |
| Routing Protocols (e.g OSPF, EIGRP) cannot pass through the VPN tunnel | Routing Protocols (e.g OSPF, EIGRP) can pass through the VPN tunnel |
| Use an access list to select which traffic is going to be encrypted and placed in VPN tunnel. | All traffic passing through a special Tunnel Interface will be encapsulated and placed in the VPN |
| Strong Security natively | GRE or VTI alone do not provide security. You must combine them with IPSEC for securing the VPN. |
| Complex Configuration | Simplified Configuration |
| Limited QoS | QoS is fully supported |
About the Writer
Harris Andrea is a network security engineer who works for a large ISP in Europe. Armed with over 15 years of experience in Cisco networking and security, Harry is a recognised Cisco engineer and holds Cisco's CCNA, CCNP and CCSP certifications. Harry maintains his own blog dedicated to Cisco networking - NetworksTraining.com and has also written a number of popular step-by-step configuration tutorials.
Back to Cisco Services & Technlogies Section
phillipskness1999.blogspot.com
Source: https://www.firewall.cx/cisco-technical-knowledgebase/cisco-services-tech/945-cisco-comparing-vpn-technologies.html
0 Response to "Easy Vpn Vs Flexvpn Vs Getvpn Vs Dmvpn"
Post a Comment